Philosophy of Security, Part 5 – Risk Management – The Process
At in the previous parts of this security series we have look at what it is , why we do it, and at some psychological factors such that affect the way we do it. Significantly, in part 4, I noted that:
… research has shown repeatedly, that our own experiences, and the constant exposure to bad news causes us to become bad at estimating the actual, as opposed to the imagined probability of threats coming to pass. Instead we focus our attention on, and give greater weight to, the things that we are bombarded with in news and media. Because of this we end up making fear driven decisions, resulting in a much higher or a much lower level of perceived safety, than the circumstances actually warrant …
It is this human predisposition to be driven by feelings of fear and safety and therefore to misinterpret the risks, that has produced numerous risk management frameworks and strategies. Some of these methodologies have have become standards, with set and pre-defined methodology and vocabulary of terms , in order to ensure that the same process and methodology is applied whenever different organisations undertake risk management activities.
In general the risk management framework and that associated process comprises of the following actions:
- Define/Discover
- Assess and Analyse Risks
- Treat/Mitigate Risks
- Watch, monitor, measure and review.
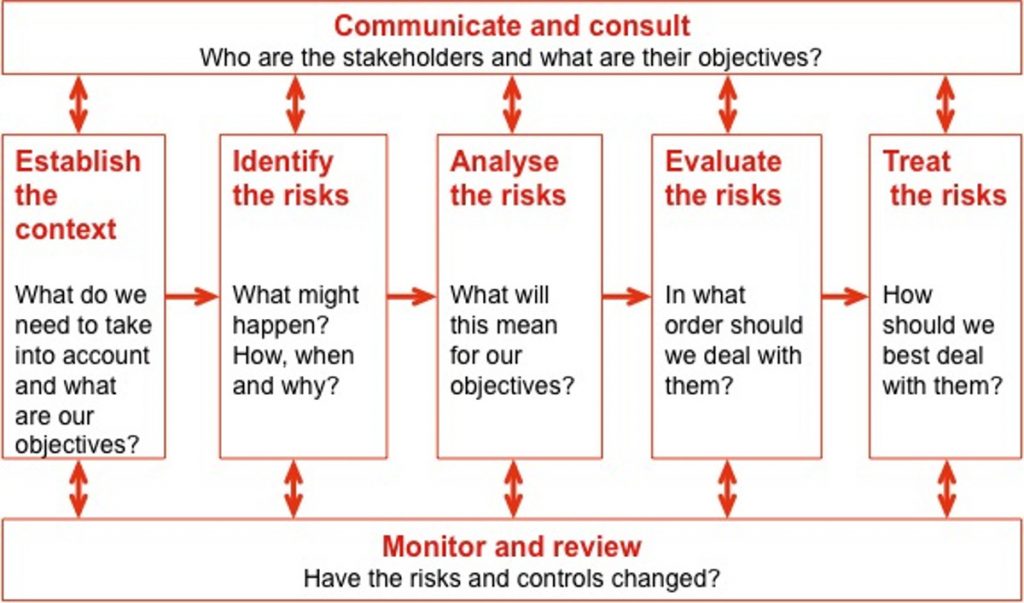
For a good example of a risk management process, is the process given in the AS/NZ standard 4630:2004 Risk Management gives the following overall process description:
Define/Discover:
1. Communicate and consult – This part of the process is concerned with communcation and consultation with the business owners and relevant stakeholders in the asset, organisation, process or system that will be subject of the risk management process. The communications are used to define context, get then necessaty information, and pass back feedback duing the risk management process.
2. Set Context – This activity is about setting collecting information avout the subject of our risk analysis and setting of the boudndries of the particular risk management activity:
- What systems, processes or assets will be considered
- Who the business owner and stakeholder are
- What are the objectives of this process
- What are the criteria we must use as part of our risk analysis.
3. Identify risks – This activity is about identifying what can happen in terms of “threats” to the asset, process or system and vulnerabilities found with the asset, process or system or in the environment around the subject of our analysis.
Assess and Analyse Risks
4. Analyse risks -Work out in as objective terms as possible, how likely a set of threats and vulnerabilities are to happen, what are current controls (i.e. what we do to stop it from occurring or how we mitigate the consequences), what are the consequences and the resultant risk level.
5. Evaluate risks – Evaluates the risks and ranks them according to the criteria set by the business owner and the stakeholders in the context setting phase.
Treat/Mitigate Risks
6. Treat Risks – Risk treatment is generally the expensive part of the risk management process, because deploying new security controls or outsourcing risk costs a lot of money. Because of this step is usually done in consultation and negotiation with the business owner and the stakeholders for each affected system, process or asset, and generally takes the form of :
- risk acceptance (do nothing new);
- implementation of additional personnel (people) , technical (locks, security alarms, firewalls) policy and procedural controls;
- transference or outsourcing of the risk to another party (e.g change to the terms of a contract, insurance policy, etc. );
Watch, monitor, measure and review.
7. Monitor and Review – This is an ongoing activity that ensures that the results of our risk management activities are what we expect them to be, and in case new threats or vulnerabilities are noticed then the resulting risks are analysed, evaluated and and treated.
Some notes on risk management process.
The critical part of the risk management process is the is the ability of the person doing the risk analysis to correctly quantify the likelihood and the consequences of the of the risk event coming to pass. This is because, as mentioned earlier, humans tend to be biased by their experiences and overall perceptions. To that end a large number of organisations often use statistical analysis.
Use of statistical data – such as actuarial tables – which hold long term statistical data about certain kinds of events such as house fires is so important to the overall risk management and its financial impact, that in some countries all insurance companies are required to provide claims and incident data to a designated 3rd party, and to use the actuarial tables produced by said 3rd party. This is done to ensure a more competitive and stable insurance industry.
Risk perception bias will necessarily arise when we attempt to derive realistic and meaningful quantitative data about a relatively new industry (or a new branch of an industry) such as web-based electronic commerce systems, for which, unlike the in case of the building or the car industry, we do not have a body of reliable information or statistical data about security issues, software flaws, or other risk factors that would allow for derivation of an actuarial style dataset on which to base our risk decisions.

1 ping
[…] previous part, Part 5 of this series we discussed the genera approaches to risk management. In this part I wish to take a […]