Philosophy of Security, part 9 – Risk Management – Risk Rating and Treatments
So far we have discussed how to quantify the likelihood of, and the impact arising form an event. In this part I would like to pull it all together and look at how we rate and prioritise risks and also look at some common approaches to risk treatments ( risk consequence mitigation and risk occurrence prevention).
Risk Rating
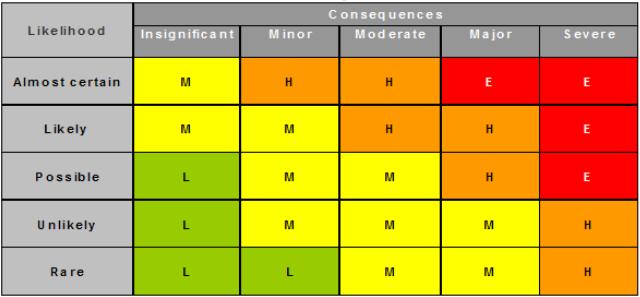
Various Risk Management standards such as the the AS/NZS and ISO Risk management standard series have prescribed risk rating methodologies. In general these methodologies rank risks using a matrix that combines a risk likelihood and risk impact to derive overall risk value. Example of such a matrix, sourced form the ISO 31000 looks a bit like this:
It is clear that for any given industry and context, industry and organisation there will be a different rating of the same event, with the same impact and frequency, based on the perceived consequences. Likewise the choice of how to treat each risk is made based on the risk management context and the overall risk appetite of the owner and the stakeholders of each business system, process or asset.
Note on Risk Appetite vs Legislation and Regulations
Organisational or personal Risk Appetite drives the risk management choices. However, there are situation in which there exists legislation or regulations which are put in place to prevent organisations from taking on more than a certain level of risk, or force us to mitigate risks in a certain way.
These sorts of regulations most commonly arise in the financial services sector, with regulations such as Basel Accord I, II and III a prime example, with force banks to maintain a certain level of in hand cleared (not debt encumbered) capital liquidity as a contingency and risk management fund which is in direct proportion to the kind of investment activity the bank engages in. Needless to say, that for some types of activity, the capital reserve requirements are very large indeed, making it quite expensive to engage in high risk behaviour.
Risk Treatments
There are several ways to treat risks, and the choice of what to do is most commonly driven by cost, regardless of the cost being expressed in terms of a terms of political or public relations cost (“We do this for the children of tomorrow!”), a reputation or customer good will cost, or a simple monetary cost, of the risk treatment put up against the likelihood and consequences of a risk event occurring. The ways in which we can deal with risks depends on the context and the stated risk appetite.
Risk treatments – also know as “security controls” come in a number of flavours and are generally described as:
- physical controls: walls, separate rooms, doors, barred windows, etc – physical barriers to prevent unwanted or unauthorised access to systems and assets.
- technical controls: things which we can use to locks, firewalls, alarms systems, anti-virus software, safes, security verification systems;
- policy controls: laws, regulations and rules within which the organisation chooses to operate. These often come with explicitly stated consequences for breach of the policy. For example policy might state that it is not permitted form employees to share computer system credentials and that the breach of this policy may be grounds for summary termination of employment.
- personnel controls: background checks on employees, to ensure they do not pose an undue reputation risk or have a history of unwanted behaviour. Examples of these are a government security clearance or a police criminal background check.
- process controls (also known as procedural controls) : these are steps inserted into process and procedures that help ensure that technical, policy, personnel and physical controls are used to full effect within a certain process. An example of this would be a person at the post office asking for photo ID before handing over an item of Registered Mail (know as Certified Mail in some places)
It is often easier to reduce the likelihood of a risk occurring than it is to to mitigate the consequences of the event.
In general, when faced with a risk we can do one of the following things:
1. Accept a risk
… “I can live with that”…
“I can live with that” should only be said, and done, in a situation where it is clear that:
- either the fact that there is little of value that can be done to prevent or mitigate the consequences of an event (war, natural disaster, etc) ;
- or the fact there are things we can do about both the possibility of the even occurreing and and all the resulting impacts and consequences of the event
are known to, communicated to, well understood and acknowledged by, the business owner and stakeholders of the business system, process or asset being managed.
This is is critical, because by accepting the risk as-is an individual or an organisation states that in their opinion there is no wish or need to spend any more time or effort on trying to prevent occurrence or mitigate the consequences the risk. By extension, such an case individual or organisation accept that there is a chance of the risk occurring, and they also accept the consequences of the event.
2. Reduce Likelihood
Reduction of likelihood (risk event avoidance) is generally easier and cheaper to achieve than risk impact minimisation. This is why there is a lot of technical controls geared around prevention, access control and compliance enforcement..
- Access control: by controlling who (organisations and individuals) has access to a business system, process or asset we are able to reduce the chances of a risk event occurring. An example of this sort of thing is an attack surface reduction approach for an web servers, where all unnecessary processes and services are removed or hidden way from access.
- Policy based treatments: These often provide a measure of deterrence, which reduces the likelihood of unwanted behaviour. For example a company mightn have a customer relationship management system usage policy witch states that the system ins monitored, and that certain behaviours will lead to immediate account suspension, an investigation and a termination of employment.
- Personnel security based treatments: only hire people who pass certain criteria for background checks for jobs in positions of that deal with large sums of money or otherwise are seen as positions of trust (teachers, child-care workers, etc.)
- Process and Procedure based treatments: Checks and balances inserted into a process which serve to validate the process, enforce policy, and uncover non-compliance.
3. Reduce Impact
Impact reduction or elimination is expensive and hard to achieve. This is why a lot of risk and security management focuses on reduction of likelihood. However, if we cannot reduce the likelihood of an event, but want to reduce the overall risk the event represents, we can do one of three things:
- Mitigate the actual impact – mitigate or reduce the impact and the consequences. Make the event less painful and damaging. For example, an organisation could encrypt all data on corporate laptops and backup tapes , so that if someone looses one of them (a large number of people leave laptops on the bus or a train), or worse yet, one of these is stolen, then the only real loss is the loss of physical property (laptop or tapes), rather than an a rather embarrassing compromise of potentially confidential corporate data such as budgets, contract details or customer data.
- Transfer risk – this is where the individual or organisation making risk management decisions transfers the risk to a third party. This often takes form of contractual damages and indemnity clauses.
- Outsource risk – to outsource the risk we pay a third party to take the risk on. The most common form of this is the insurance, where we pay someone a small premium, so that they compensate us when something bad happens.